
THE PROBLEM
The Intelligence and Surveillance Community do things behind your back without you knowing. AGENCIES of the United States and FEDERAL AGENTS in their official capacities are immune from suit for constitutional violations. With the latest military technology they use COVERT ACTION to exploit and analyze ANYBODY with NO ACCOUNTABILITY.
ELECTRONIC MONITORING is done remotely and can make it difficult for people to function normally. Examples are job interviews, access employment and education, receive medical treatment, responsibly parent their children, or take part in family and community life.
COVERT ACTION DESTROYS LIVES and can leave people and groups with nothing left. There is a community of people who harass people to commit crimes or "stage" terrorist acts. We have a major refugee, homeless, and mental health crisis with no solutions thanks to them.
WHAT IS ELECTRONIC MONITORING
SENATE HEARING PRESENTATION
INTERVIEW WITH A GANG STALKER
TESTIMONIES OF TARGETED INDIVIDUALS
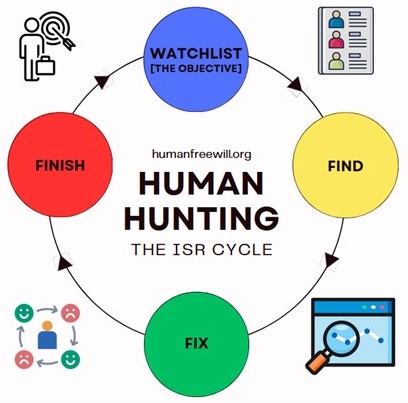
THE HUMAN HUNTING CYCLE
INTELLIGENCE GATHERING FOR INFORMATION
BIOMETRIC INFORMATION is PERSONAL INFORMATION (DNA, voice, face, parts of the body). There are organizations that collect and store your information for "business purposes". An example is the Automated Biometric Information System, or ABIS, which stores and queries millions of peoples' biometric files collected both domestically and abroad. According to a report from the Government Accountability Office, the joint FBI/Defense Department facility can screen an individual through both the military's massive ABIS and the FBI's sprawling fingerprint database, known as IAFIS. “The IAFIS database includes the fingerprint records of more than 51 million persons who have been arrested in the United States as well as information submitted by other agencies such as the Department of Homeland Security, the Department of State, and Interpol,” the report reads.
Anytime you've got a center that's combining two operations of criminal enforcement and national security there's a risk and almost a certainty of blurring lines and running afoul of what is allowed in a law enforcement context (CHAOS).
- PRIVACY IS IMPOSSIBLE WHEN TARGETING WITH BIOMETRIC SURVEILLANCE
INTELLIGENCE GATHERING FOR EXPLOITATION
The Intelligence, Surveillance, and Reconnaissance (ISR) Cycle is a 24/7 365 on going enterprise of human exploitation. YOUR FATE is determined by who surveils you because it is a "joint" team effort of continually tracking and staging events. Extraordinary Renditions are when they completely isolate a person and control the flow of INFORMATION over a prolonged period of time to "influence" events. These FORCES end up countering any forward progress for certain communities because the goal is to keep people vulnerable and marginalized so they are easier to manipulate.
In the early 1970's, in a climate altogether unlike today's, the intelligence-gathering and surveillance activities of the NSA, the FBI, and the CIA came under public scrutiny. The Supreme Court struck down certain warrantless surveillance procedures that the government had argued were unlawful as an exercise of the President's power to protect national security, remarking on "the inherent vagueness of the domestic security concept [and] the necessarily broad and continuing nature of intelligence gathering".
- INFORMATION OPERATIONS WILL HIDE WHAT IS IMPORTANT FROM TARGETED COMMUNITIES
OUR MISSION
END WARRANTLESS SURVEILLANCE for human exploitation. DEMOCRACY DIES IN DARKNESS with INFORMATION OPERATIONS hiding the truth.
COVERT ACTION WITH NO DUE PROCESS CAUSES:
- in suicides
- in mass murders
- in homelessness
- in the mental health crisis
they destroy lives then repeat the cycle on someone new
children are also targeted to impact communities for generations
Human Free Will is a 501(c)(3) Non-Profit that helps victims of covert action learn about the associated methods and technology. NO ACCOUNTABILITY to society the list of victims will only grow.
"We're at war right here at home and it's our own government."
-
WE HAVE LAWSUITS, GUIDES, AND MEETUPS THAT FOCUS ON:
- SURVEILLANCE, HARASSMENT, AND INFORMATION OPERATIONS
WHO WE SERVE
If you are "labeled" as a threat you can experience 24/7 365 automated unending covert harassment with NO DUE PROCESS. With unlimited time and public funding, these "gang of stalkers" use military surveillance technology to make and keep people vulnerable. RENDITIONS, DETENTIONS, and INTERROGATIONS are now done remotely over the electromagnetic spectrum. EVERYTHING in nature is an exchange of energy and scientific forces (when directed) can remotely cause a mental health crisis. TARGETED INDIVIDUALS are subjected to constant interference for HUMAN EXPLOITATION to torture and ruin their life and those around them with NO JURISDICTION to turn to.

I, sitting at my desk, could wiretap anyone, from you or your accountant, to a federal judge or even the President, if I had a personal e-mail. THE CAPABILITY, WITHOUT A WARRANT, TO SEARCH FOR, SEIZE, AND READ YOUR COMMUNICATIONS. ANYONE'S COMMUNICATIONS AT ANY TIME. THAT IS THE POWER TO CHANGE PEOPLE'S FATES.
OUR VISION
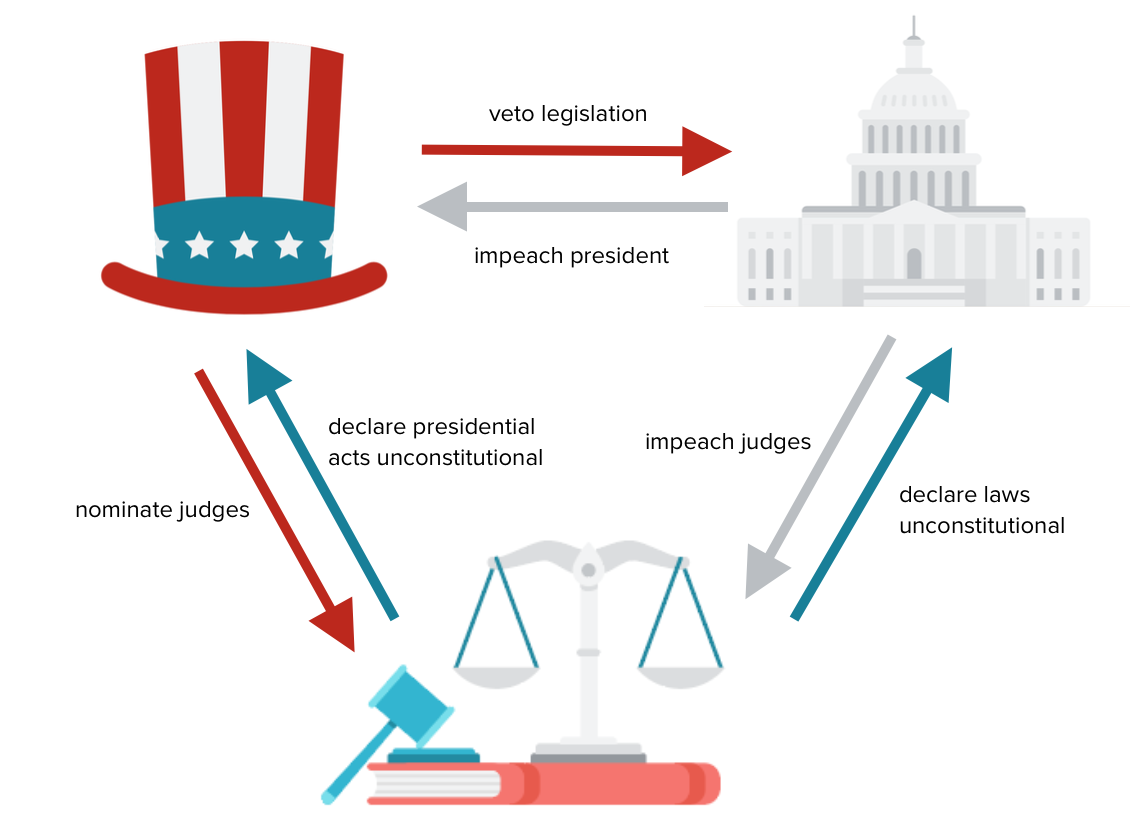
The Constitution of the United States is currently being misinterpreted from what our Founding Fathers intended. THE SYSTEM of checks and balances is intended to prevent abuse of power and to ensure that the government remains accountable to the people. There are "competing forces" outside of the Executive, Legislative, and Judicial branches of government. These are "leaders" with NO ACCOUNTABILITY who are currently making decisions for you and your community. With sanctioned COVERT ACTION we CAN NOT count on the Executive or Judicial branches. We are trying to raise enough awareness for a modern-day Rockefeller, Church, and Pike Committee in the Legislative branch to END WARRANTLESS SURVEILLANCE for "staging" WAR ON TERROR events. Regulations need to be put in place for the private sector. NEVER once held accountable for ANY "targeting" decisions, agents and analysts retire to continue to EXPLOIT every community for future generations.
PERMANENT RECORD
BY EDWARD SNOWDEN
On Constitution Day 2012, I picked up the document in earnest. I hadn't really read the whole thing in quite a few years, though I was glad to note that I still knew the preamble by heart. Now, however, I read through it in its entirety, from the Articles to the Amendments. I was surprised to be reminded that fully 50 percent of the Bill of Rights, the document's first ten amendments, were intended to make the job of law enforcement harder. The Fourth, Fifth, Sixth, Seventh, and Eighth Amendments were all deliberately, carefully designed to create inefficiencies and hamper the government's ability to exercise its power and conduct surveillance.
This is especially true of the Fourth, which protects people and their property from government scrutiny. The right of the people to be secure in their persons, houses, papers, and effects, against unreasonable searches and seizures, shall not be violated, and no Warrants shall issue, but upon probable cause, supported by Oath or affirmation, and particularly describing the place to be searched, and the persons or things to be seized.
COVERT ACTION
If "leaders" are only good at the ISR Cycle and Information Operations to cover it up, what happens to society as a whole? The answer today is to do more ISR Cycle and Information Operations so NO ONE knows.
Subscribe to the Newsletter
We are approaching an inflection point in Human History. Get the latest insights. From business to the quantum details. We try to explain the "effects". Hopefully the truth gets communicated.