COMMUNICATION NETWORKS
FROM THE DRONE PAPERS
MAN IN THE MIDDLE NETWORK ATTACKS
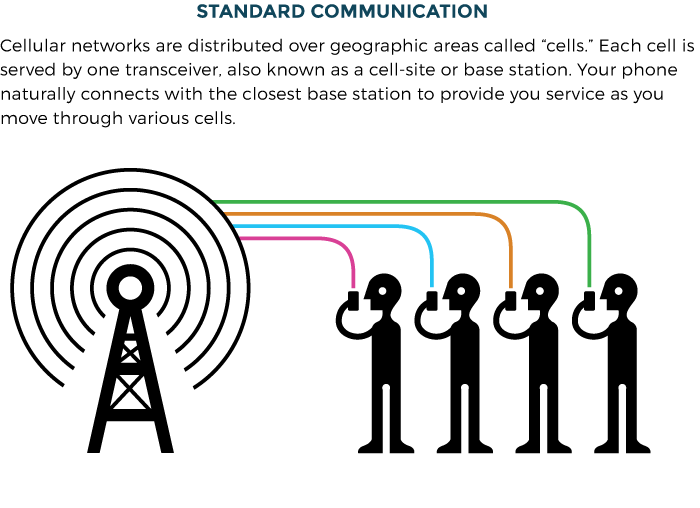
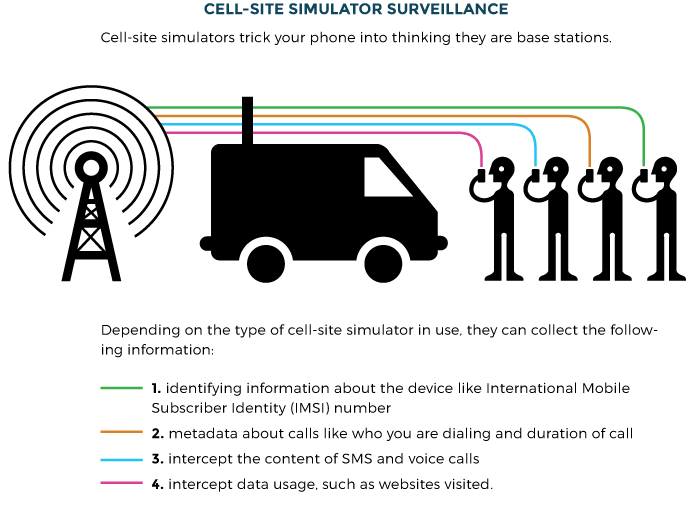
THERE IS NO WAY FOR ASSURED PRIVACY
EVEN WITH ENCRYPTION SERVICES YOU NEED TO VERIFY
WITH MAN IN THE MIDDLE YOU DON'T KNOW WHAT YOU ARE DOWNLOADING
OUR PACKET TRACES FOUND SOFTWARE WAS NOT ENCRYPTING ANY TRAFFIC
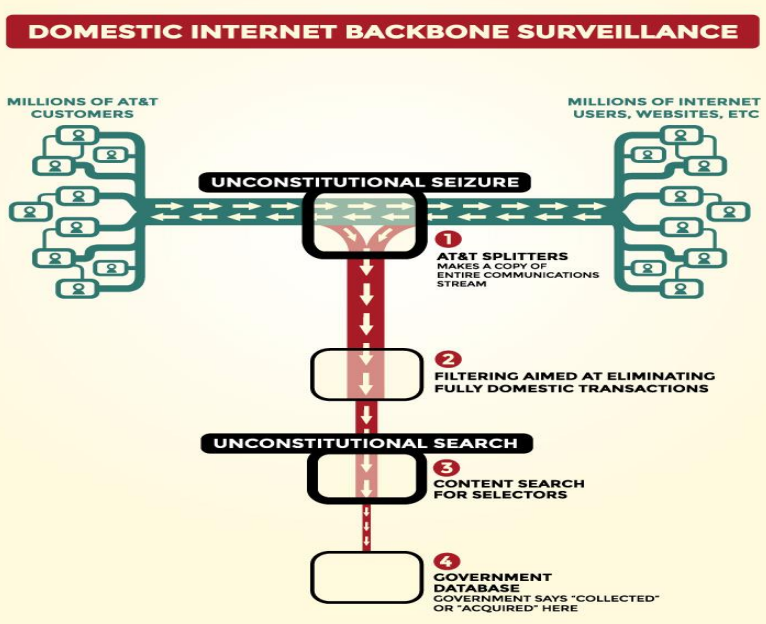
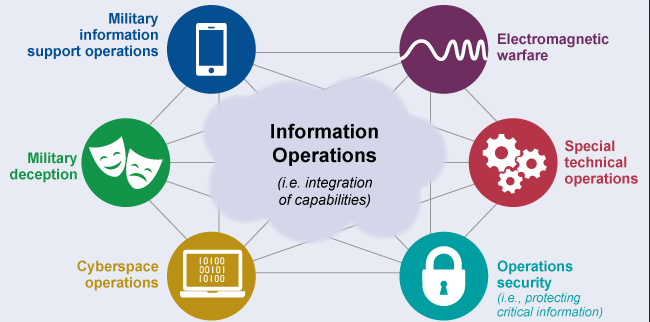
INFORMATION OPERATIONS control the flow of communications. The Intelligence, Surveillance, and Reconnaissance (ISR) Cycle is a 24/7 365 on going enterprise of hiding what is important and replacing it with distractions. INFORMATION can be used to TAKE ADVANTAGE of people or groups by changing beliefs. RENDITIONS, DETENTIONS, and INTERROGATIONS are now done remotely over the electromagnetic spectrum without anyone even knowing. Once "targeted" all forms of communications can be blocked or have useful INFORMATION changed to influence.
"There exists a shadowy government with its own Air Force, its own Navy, its own fundraising mechanism, and the ability to pursue its own ideas of national interest, free from all checks and balances, and free from the law itself."
CONTROLLING ALL COMMUNICATION METHODS
ELECTRONIC INFORMATION CAN EASILY BE BLOCKED
ELECTRONIC INFORMATION CAN EASILY BE ALTERED
reason we are providing PDF documents instead of links to other sites
MILITARY BANS NEWS
CELL SITE SIMULATORS
WHAT IS ELECTRONIC WARFARE
ELECTRONIC WARFARE ON PROTESTORS
CONNECTED TO UNKNOWN NETWORK

LAWSUITS ARE GOOD SOURCES OF INFORMATION
HUMAN FREE WILL v. RCN & SERVICE ELECTRIC (2022)
[TO GET OFF PRIVATE NETWORK FOR ATTACKS]
ALL FORMS OF COMMUNICATIONS GET BLOCKED OR REROUTED
PRIVATE NETWORK IS A MAN IN THE MIDDLE KEEPING IN DETENTION
HUMAN FREE WILL v. JOHN DOE AGENCY et al (2022)
[INVESTIGATION INTO CONSTANT COVERT ATTACKS]
WE HAVE NEVER RECEIVED ANY OFFICIAL NOTICES IN THE MAIL
WE HAVE NEVER BEEN ABLE TO ACCESS THE ONLINE PORTAL
STATE OF MARYLAND v. ANDREWS (2016)
[WARRANTLESS SURVEILLANCE USING CELL SITE SIMULATOR]
first case in the country where an appellate court held that the use of the device without a warrant violated the Fourth Amendment right to be free from unlawful searches and seizures
JEWEL v. NATIONAL SECURITY AGENCY et al (2011)
[WARRANTLESS MASS SURVEILLANCE USING NETWORK PROVIDERS]
largest known case with the outcome eventually making warrantless mass surveillance legal
MOST PEOPLE YOU KNOW ARE NOT GOOD SOURCES OF INFORMATION
COINTELPRO
Counter Intelligence Programs targeted minority groups of local and national prominence as part of organized resistance to their struggles to secure civil rights for all Americans. In 1976, the Senate Select Committee on Intelligence (the Church Committee) issued a report documenting systematic violations of civil rights by the FBI and other intelligence and security organizations. It is well known, for example, that the FBI expended considerable resources attempting to undermine the work of Dr. King by linking him to allegedly subversive organizations and by discovering details of his personal life.
This is public INFORMATION. What is NOT known is what is EVERYONE that got away doing now? ALOT has happened in science and technology over the past 50 years. This COMMUNITY that doesn't give back to society has grown. Do you just stop ruining lives?
Subscribe to the Newsletter
We are approaching an inflection point in Human History. Get the latest insights. From business to the quantum details. We try to explain the "effects". Hopefully the truth gets communicated.